Vulnerability Handling Process
Midea Home Appliances UK Ltd. LIFESTYLE PRODUCTS & SERVICES CORPORATION (The following will be referred to as Midea Home Appliances UK Ltd.) is committed to enhancing the safety of its products and fully supports the secure operation of its customer networks and businesses. The company places great importance on vulnerability management in product development and maintenance, and follows ISO/IEC 30111, ISO/IEC 29147 and other standards to establish a complete vulnerability handling process to enhance product safety and ensure timely response when vulnerabilities are discovered.
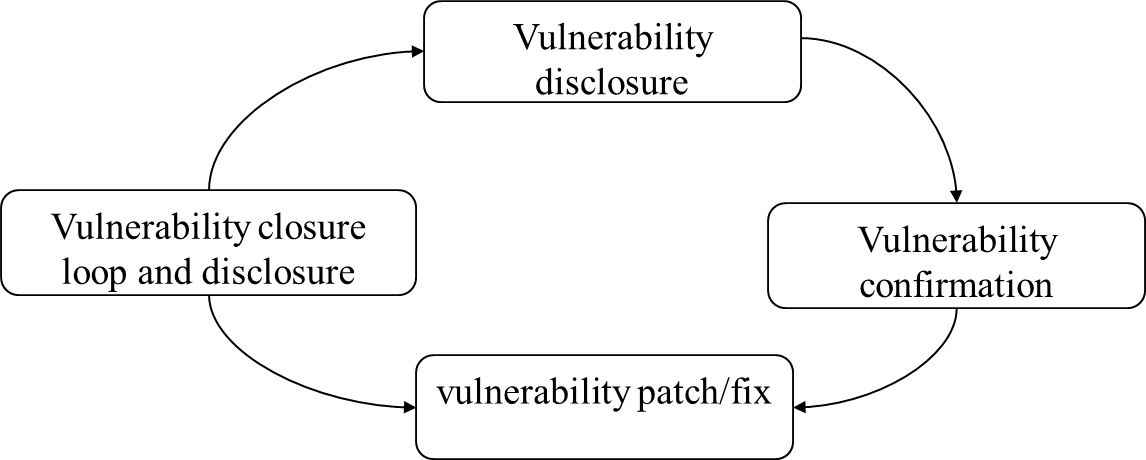
- Vulnerability reception:We accept and gather information about potential product vulnerabilities.
- Vulnerability confirmation: We confirm the validity and scope of the suspected vulnerabilities.
- Vulnerability repair:We develop and execute a plan to rectify identified vulnerabilities.
- Vulnerability closure and announcement information release: We release information about the vulnerability remediation to our customers and use their feedback and our own experience to continuously improve our processes.
Vulnerability Reporting Channel
If you believe that you have discovered a security or privacy vulnerability in the products of Midea Home Appliances UK Ltd., you can fill out the template and send the security issue directly to: appdpo@global.toshiba-lifestyle.com.
Vulnerability Confirmation
Midea Home Appliances UK Ltd. LIFESTYLE PRODUCTS & SERVICES CORPORATION (The following will be referred to as Midea Home Appliances UK Ltd.) is committed to enhancing the safety of its products and fully supports the secure operation of its customer networks and businesses. The company places great importance on vulnerability management in product development and maintenance, and follows ISO/IEC 30111, ISO/IEC 29147 and other standards to establish a complete vulnerability handling process to enhance product safety and ensure timely response when vulnerabilities are discovered.
Vulnerability Fix
The security team of Midea Home Appliances UK Ltd. will analyze and verify vulnerabilities together with the product team, evaluate the severity level of the vulnerabilities based on their actual impact on the product, determine the priority of patches, and develop vulnerability remediation plans (including mitigation measures, patches/versions, and other risk reduction plans that customers can execute). We will regularly update the vulnerability reporter on the progress of vulnerability fixes, and based on the principles of minimizing harm and reducing risk, we will release vulnerability information to stakeholders to support customers in assessing the actual risk of vulnerabilities to their networks.
Vulnerability Closure and Announcement
The enterprise confirms the vulnerability fix and closes the vulnerability. After the vulnerability lifecycle ends, relevant information and repair methods will be announced in the“Security Bulletins”. And we will send an email to the user who submitted the vulnerability to inform them that the vulnerability they submitted has been fixed.
Throughout the vulnerability handling process, the emergency response team of Midea Home Appliances UK Ltd. will strictly control the scope of vulnerability information and only pass it on among relevant personnel handling the vulnerability. At the same time, we also request that reporters keep the vulnerability information confidential until our customers obtain a complete solution. The company will take necessary and reasonable measures to protect the data obtained in accordance with legal and compliance requirements. Unless specifically requested by affected customers or required by law, the above data will not be shared or disclosed to other parties proactively.
Severity Assessment of Vulnerabilities
Based on the comprehensive score of the Security Severity Rating (SSR) vulnerability severity level assessment, Midea Home Appliances UK Ltd. classifies vulnerabilities into five levels: Critical, High, Medium, Low, and Informational.
Critical-level security issues
- Directly obtaining core system privileges. These vulnerabilities can directly jeopardize the internal network and may include, but are not limited to, command execution and remote overflow;
- Vulnerabilities that can obtain a large amount of user core data.
- Logic vulnerabilities that directly cause serious impact. Related vulnerabilities include but are not limited to serious logic errors, and vulnerabilities that can cause significant losses to the company and users.
High-level security issues
- Vulnerabilities that allow direct access to business server permissions, including but not limited to arbitrary command execution, webshell uploads, and arbitrary code execution;
- Vulnerabilities that directly result in serious information leaks, including but not limited to SQL injection vulnerabilities in core databases.
- Logic vulnerabilities that directly result in significant impact, including but not limited to vulnerabilities that allow arbitrary changes to account passwords.
- Vulnerabilities that could lead to mass theft of user identity information, such as SQL injection.
- Unauthorized access, including but not limited to bypassing authentication to access the backend.
Medium level security issues
- Vulnerabilities that require interaction to obtain user identity information, including but not limited to stored XSS vulnerabilities.
- Arbitrary file operation vulnerabilities, including but not limited to arbitrary file reading, writing, deletion, downloading, etc..
- Unauthorized access, such as bypassing restrictions to modify user information or execute user operations.
- Relatively serious information leakage vulnerabilities, including the leakage of sensitive information files (such as DB connection passwords).
Low level security issues
- Vulnerabilities that can cause certain impacts, but do not directly affect device permissions or data security. These may include minor information leakage, URL redirection, less exploitable XSS vulnerabilities, and common CSRF vulnerabilities.
Information-related issues
- Bugs that do not involve security issues, including but not limited to product function defects, webpage garbled code, style disorder, static file directory traversal, application compatibility issues, etc..
- Vulnerabilities that cannot be exploited, such as CSRF without sensitive operations, meaningless abnormal information leakage, internal IP address/domain name leakage.
- Other issues that do not directly indicate the existence of vulnerabilities, such as issues based purely on user speculation.
Third-party software vulnerabilities
Due to the diversity of integration methods and scenarios of third-party software/components in Midea Home Appliances UK Ltd. products, the company will adjust the vulnerability rating of third-party software/components according to the specific scenarios of the product to reflect the true impact of the vulnerability. For example, if an affected module of a certain third-party software or component is not in use, the associated vulnerability would be considered 'unexploitable and unaffected'.If the existing evaluation system cannot cover the dimensions of evaluation, Midea Home Appliances UK Ltd. is responsible for explaining the evaluation results.
If the following three criteria are met at the same time, Midea Home Appliances UK Ltd. will identify the vulnerability as "High Profile":
- CVSS score is 5.0 or above.
- The vulnerability has attracted widespread public attention.
- The vulnerability is likely or already has available exploits, and may or is being actively exploited.
For "High Profile" third-party vulnerabilities, Midea Home Appliances UK Ltd. will check all product versions, and after confirming the vulnerability as "High Profile", it will release SN (Security Notice) within 24 hours to notify relevant customers of Midea Home Appliances UK Ltd.'s handling of the vulnerability. When there is a vulnerability patch solution, Midea Home Appliances UK Ltd. will provide risk decision-making and mitigation support for affected customers through SA (Security Announcement). For third-party vulnerabilities that are not classified as "High Profile", the company will explain them in the version/patch instructions.
Release of Vulnerability Information Notice
There are two ways in which Midea Home Appliances UK Ltd. discloses security vulnerabilities in its products:
- Security Advisory (SA): When a vulnerability is confirmed, we disclose detailed vulnerability information and corresponding remediation measures through an SA.
- Security Notification (SN): When a potential vulnerability is discovered or noticed externally, but not yet confirmed, we disclose basic information about the vulnerability and our investigation progress through an SN. Vulnerability information should be kept confidential until Midea Home Appliances UK Ltd. releases a security advisory or security notification to the public.
Announcement Plan
When one or more of the following conditions are met, Midea Home Appliances UK Ltd. will release an SN or SA to provide customers with real-time risk decision support:
- The Security Severity Rating (SSR) is defined as "Critical" or "High" vulnerabilities. Midea Home Appliances UK Ltd. has completed the vulnerability response process and can provide vulnerability patch support to customers to reduce real-time risks.
- Midea Home Appliances UK Ltd. will accelerate response process if a vulnerability in the product version of Midea Home Appliances UK Ltd. may attract widespread public attention, has been observed to be actively exploited, or could increase the risk to our customers,Midea Home Appliances UK Ltd. will notify customers within 24 hours of meeting the above conditions, and continuously update the vulnerability response progress.
Security Update
Please update your applications and devices in a timely manner, as this is one of the most important measures to maintain the security of Midea Home Appliances UK Ltd. products. Obtain the latest software updates from the official website:
For specific product/software version vulnerability fixes, please refer to the announcement: jump to the security notice page.
Disclaimer & Reservation of Rights
- The policy described in this article does not constitute a guarantee or promise, nor does it constitute any part of a contract. Midea Home Appliances UK Ltd. reserves the right to adjust the above policy at its discretion.
- Midea Home Appliances UK Ltd. reserves the right to change or update this document at any time. We will update this policy statement as necessary to increase transparency or respond more actively to feedback from customers, regulatory agencies, industries, or other stakeholders, such as:
- Changes to the overall policy.
- Introduction of best practices, etc.
- When changes to this policy statement are published, we will revise the "Update Date" at the bottom of this policy.
Definition
The following definitions are used in this strategy:
Name |
Definition |
ISO/IEC 29147 |
The disclosure of potential vulnerabilities guidelines developed by the International Organization for Standardization |
ISO/IEC 30111 |
Vulnerability management process developed by the International Organization for Standardization (ISO) |
CVSS |
Common Vulnerability Scoring System |
SSR |
Security Severity Rating |
online risk |
There are various security threats and risks on the Internet, including but not limited to cyber attacks, data breaches, phishing, malware, identity theft, etc. These risks may result in adverse consequences such as economic losses, reputational damage, and information leakage for individuals, businesses, organizations, etc. In order to reduce the risks on the Internet, people need to take a series of measures, such as using strong passwords, regularly updating software, installing anti-virus software, and not easily disclosing personal information. |